Home » Data protection and IT security issues with age verification app „Yoti“
This article is also available in German.
An investigation from Mint Secure GmbH reveals that one of the leading age verification and age estimation apps “Yoti” is extensively tracking users without consent, likely in violation of the EU General Data Protection Regulation (GDPR). The investigation raises the question of how credible the company’s data protection efforts are and shows how fragile an age estimation tool potentially can be if the training data and supply chain can be manipulated.
Important: The information presented in this article was collected on June 4, 2025 and is supplemented by updates and feedback from the responsible body (Yoti) at the end of the article.
This article starts with a short introduction into age estimation and verification software and then continues with an investigation of Yoti’s website, Android app and an inspection of elements from the AI models in use.
In the European Union, age estimation and verification have become central to digital policy as regulators seek to protect minors online. The European Commission is developing an age verification app, which will allow users to prove their age based on digital identities. This app, a precursor to the EU’s digital identity wallet due in 2026, aims to provide a secure and private age verification method for online services seeking to keep underage users off their platform. While the EU hasn’t introduced age verification mandates, very large online platforms and search engines are obliged to mitigate systemic risks relating to the protection of minors under the Digital Services Act. The Electronic Frontier Foundation (EFF) has raised concerns about the potential for such systems to infringe on all users’ privacy and freedom of expression, advocating for protective alternatives that do not require age checks . The debate continues as the EU seeks to balance child protection with fundamental rights.
This investigation examines Yoti, a leading provider of age verification and age estimation technology, self-described as privacy-focused, to outline privacy and security challenges in implementations of age verification and age estimation apps.
Yoti is a service provider for identity verification and over the last years has also specialized on age verification and facial age estimation. On the company website Yoti describes itself: “Yoti is a digital identity company that makes it safer for people to prove who they are. We started by empowering people with a free, reusable digital ID app that minimises the data they share with businesses.” Furthermore they outline one of their services as: “A privacy-first approach to age verification”.
Yoti has 2 main solutions for age determination:
• Age Verification (mostly based on ID-cards, credit card check, mobile provider or database check)
• Facial Age Estimation (based on video-selfies)
Both solutions are implemented in the Yoti App, furthermore they can be integrated in third party software with SDKs .
Yoti is a leading provider of age verification and age estimation technology. On its Google Play Store profile, Yoti claims to have “over 14 million downloads” for the “Yoti – your digital identity”-App. Furthermore, in other marketing material Yoti claims to have executed more than 500 million checks in total . Major social media platforms like Meta’s Instagram have implemented Yoti as an age verification or estimation solution in several countries, including the European Union.
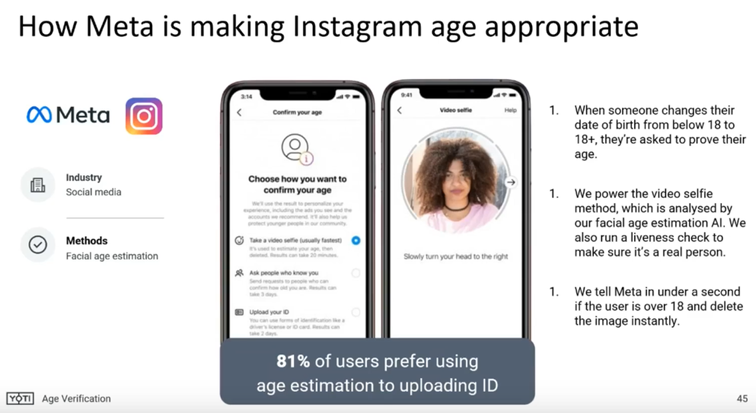
Other clients include Sony PlayStation, French social networking app Yubo, EpicGames and adult sites XHamster and OnlyFans (pictures taken from: https://youtu.be/3VEsjFN_iSM?t=263).
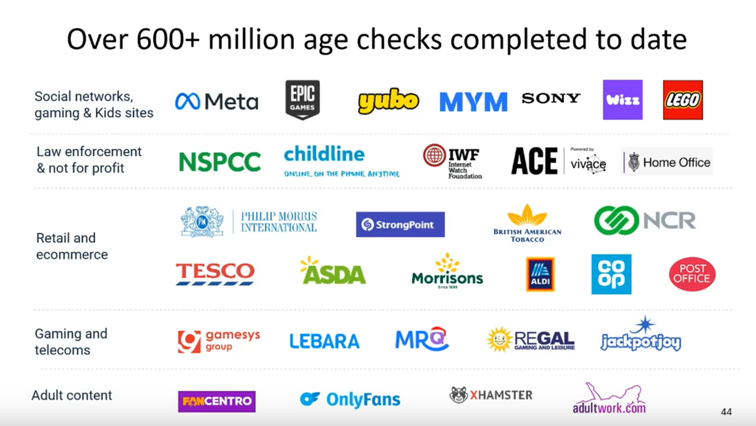
Yoti’s expansive customerbase warrants a close examination of whether Yoti’s privacy promises are fulfilled, how serious Yoti takes users privacy and how secure the AI models and implemented protections are.
While visiting the website of Yoti (yoti.com) the first time one can see that immediately a cookie banner appears and asks for acceptance of cookies.
While it is positive that Yoti does not try to nudge users with dark patterns or similar techniques, a view in the network traffic tab is very disappointing. When observing the network traffic in the background one can identify that multiple connections to third parties are already established without any click in the Cookie Banner or the consent of the user (even after clicking “Reject all” this behavior takes place). In short: The Cookie Banner seems not to be implemented correctly and third-party applications are directly loaded without any interaction.
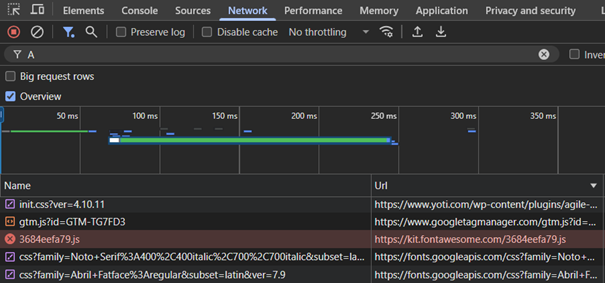
The following network requests are made regarding these resources:
– Google Tag Manager: https://www.googletagmanager.com/gtm.js?id=GTM-TG7FD3
– Fontawesome: https://kit.fontawesome.com/3684eefa79.js
– Google Fonts hosted on googleapis.com: https://fonts.googleapis.com/css?family=Noto+Serif%3A400%2C400italic%2C700%2C700italic&subset=latin%2Clatin-ext&ver=6.7.1 & https://fonts.googleapis.com/css?family=Abril+Fatface%3Aregular&subset=latin&ver=7.9
– Jquery hosted on googleapis.com: https://ajax.googleapis.com/ajax/libs/jquery/3.7.1/jquery.min.js
Transferring personal identifiable information like a user’s IP address to a third party without the user’s consent likely violates the GDPR. According to Article 7 of the GDPR, consent must be freely given, specific, informed and unambiguous . In the past, German courts have ruled that loading Google Fonts from Googles webservers is unlawful if no user consent has been given . A privacy-friendly default setting is that consent should always be designed as an opt-in. This means that consent (to data processing) must not be pre-selected or automatically enforced.
Ironically, even when navigating directly to the Yoti Privacy Center (https://www.yoti.com/privacy/), these resources are still loaded – an important detail for the subsequent analysis of the app.
As mentioned above, Yoti has an app since 2016 to provide service to end users, which, according to Yoti, has been downloaded more than 14 million times.
The investigated Android app „com.yoti.mobile.android.live“ was published on 26 May 2025 (version: 3.69.0).
The following data is provided for anyone who wants to reproduce the results described:
Name: com.yoti.mobile.android.live.apk
Size: 60307312 Bytes (57 MB)
SHA256: 8EC516DA0C6F9DBEFC3BE4AA1E4C37D782566CB3BE28D3C2C9C3985B9991606F
A first statical analysis with the privacy tool „Exodus Privacy“ via code analysis reveals that very likely 4 trackers are included in the app directly :
To ensure that this information is accurate, a dynamic test via runtime was performed with a custom tool and the App „TC Slim“ (TrackerControl) which acts as a man-in-the-middle proxy to view the network traffic, when launching the app.
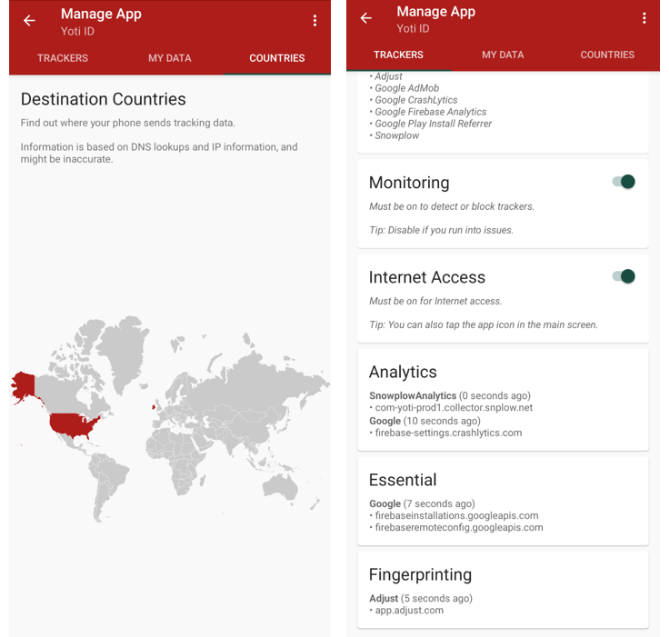
It was found that the following resources are loaded directly after starting the app, without any user consent and without comprehensive interaction with the app:
These requests are again likely a violation of the GDPR, because third party providers are requested without any legal basis or consent from the users and sensible information are transferred (like Advertising-IDs and an Universally Unique Identifier (UUID)). The Advertising ID is uniquely linked to a specific device. It can be used to build a user profile based on behavior across apps, websites, and over time. Even if the ID doesn’t directly reveal a name, it can be combined with other data to identify a person.
The used Tracker “Adjust” collects the following information about the device in use:
Device Manufacturer: Google
Android UUID: 9f1b2c48-8d45-4e32-942c-3a1a9bfe1f09
Referrer (Source of Installation): Google Play Store
Google Advertising ID: a57c4db3-91f2-478b-ae3c-cc5dbe9d12a4
Operating System: Android
Display Resolution: 1344×2992
Tracking Enabled: 1
Hardware Name: google_coral-user 14 AP1A.240405.002 1234567
Package Name: com.yoti.mobile.android.live
App Version: 3.69.0
Device Name: Pixel 8 Pro
OS Version: 14
CPU: arm64-v8a
[…]
This collection of data constitutes a nearly unique fingerprint of the mobile device. It allows third parties to reliably recognize the same device across different contexts, even if the user does not explicitly identify themselves. Of particular concern is the Google Advertising ID. Although it is marketed as a „resettable“ identifier meant for advertising purposes, in practice, it can be used to correlate activity across multiple apps. If various apps on a user’s phone share this identifier with external services or data brokers, these parties can link the user’s behavior across different applications, potentially building a detailed profile of interests, habits, and even sensitive information – such as whether the user has installed apps related to health, finance, or identity verification like Yoti.
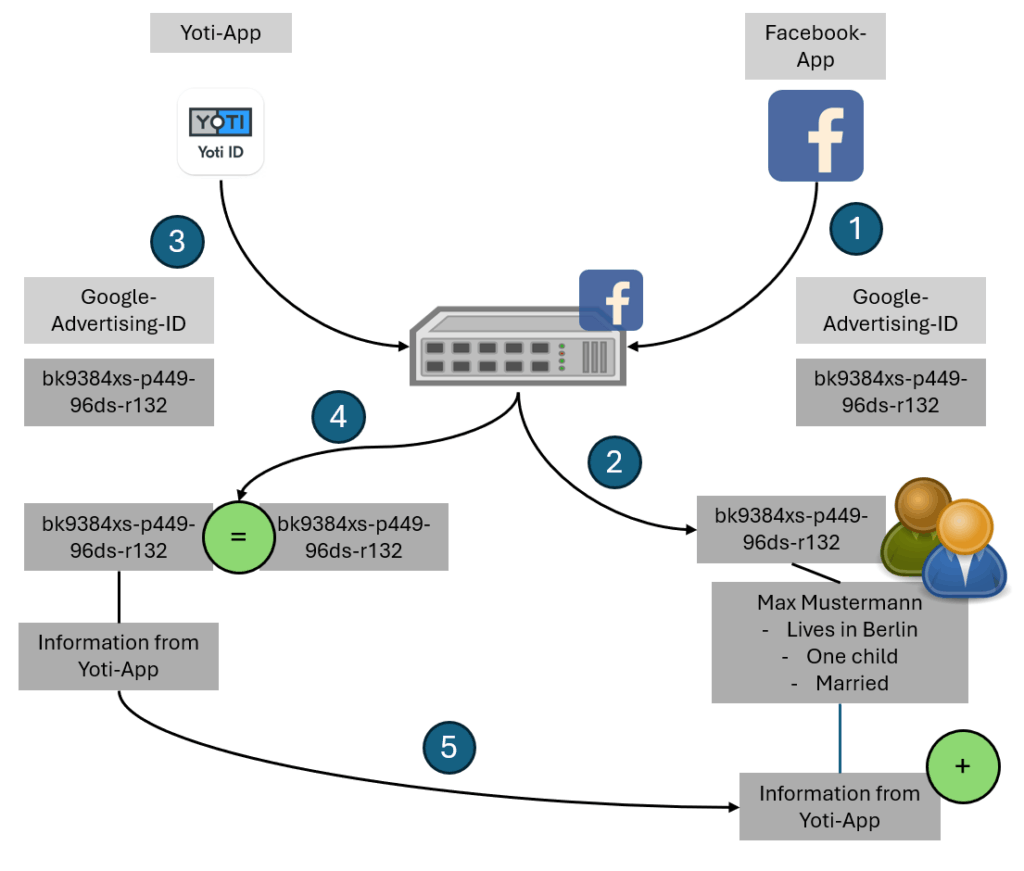
The following graphic (based on Kuketz-Blog) show how a tracking / linkability like that can take place:
1. The user uses an app which captures the Advertising-ID.
2. A databroker combines the user data with existing information.
3. The user installs the Yoti app and the Advertising-ID is processed.
4. It’s recognizable that the same Advertising-ID is linkable to other activities.
5. Information about the installation of the Yoti app and even more action can be added to existing data.
The inclusion of stable identifiers like the Android UUID, detailed hardware name, and screen resolution increases the risk further, as these can be used for persistent tracking even if the user resets their Advertising ID. This undermines user consent and privacy expectations. In short, when such identifiers are collected and shared without strong limitations, they pose a serious threat to user privacy, enabling long-term behavioral profiling, targeted manipulation, and potential re-identification – even if the data is ostensibly “pseudonymous”.
Yoti is not asking for consent to use the advertisement ID via Adjust. Yoti’s privacy policy does mention that such data collection takes place – but does not outline or describe the risk associated with this type of data collection any further :
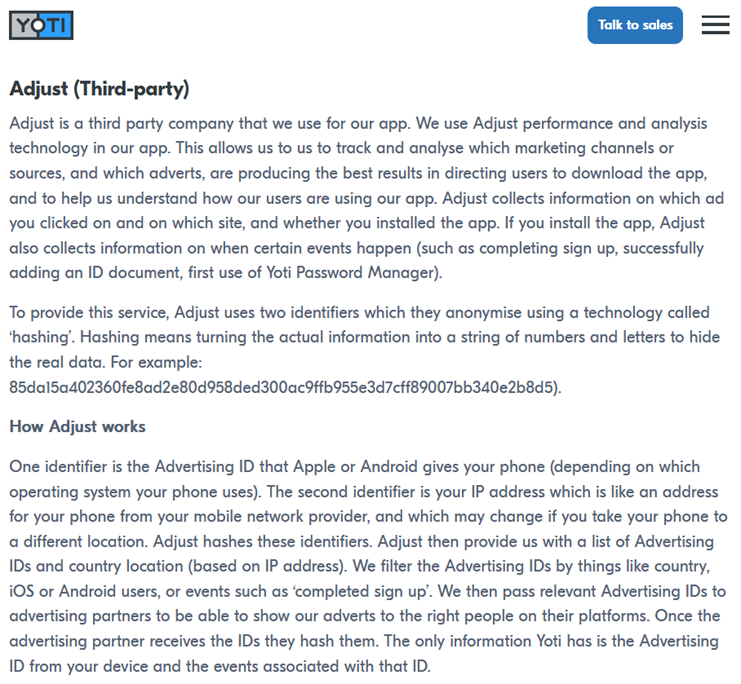
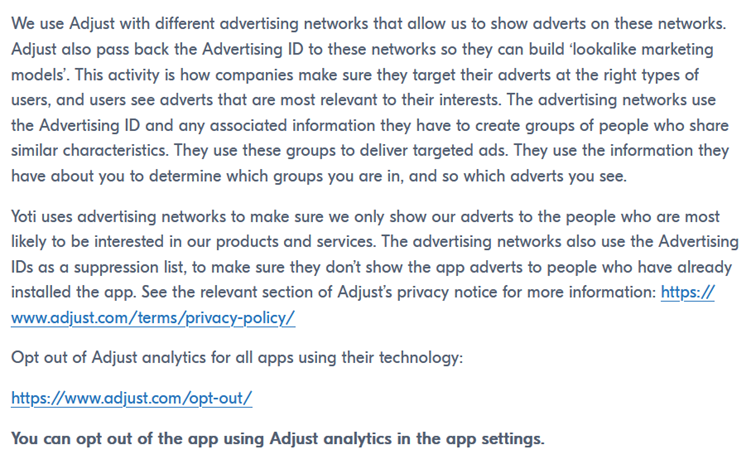
As one can see at some points in the privacy policy it is mentioned that hashing is used to “protect” information. While a clearer concept description for that is missing and at other points also a processing of the Advertising ID is described there are further issues with hashing: Hashing is often misunderstood as a foolproof way to protect user data, but it still carries significant privacy risks. Although hashing transforms information into an unreadable string, it does not make the data truly anonymous. If the original information – such as advertising identifiers or common user actions – is predictable or drawn from a limited set, attackers can use techniques like dictionary attacks or rainbow tables to reverse the hash and recover the original data. Furthermore, hashed identifiers can still be used to track users over time because they remain consistent, enabling behavioral profiling even without knowing the user’s real identity.
This undermines user privacy and makes hashing a form of pseudonymization rather than true anonymization. Additionally, if the hashing algorithm is outdated or implemented without added randomization (like salting), the data becomes even more vulnerable. Overall, while hashing adds a layer of protection, it is not sufficient on its own to guarantee user privacy or compliance with stricter data protection standards.
Furthermore, the default opt-in into Adjust is not privacy friendly. At least a consent via an in-app cookie banner needs to be implemented to achieve compliance with the GDPR – or even better: not using trackers like that at all – if one claims to provide “A privacy-first approach to age verification”.
The other trackers in the app are also sending sensitive information from the devices to third parties, like Google Firebase which was criticized in the past.
Next to the trackers „Exodus Privacy“ also revealed that there are very extensive permissions, this could also independently be verified by a review of the “AndroidManifest.xml” of the app.
The permissions claimed are the following:
– ACCESS_ADSERVICES_AD_ID
– ACCESS_ADSERVICES_ATTRIBUTION
– ACCESS_COARSE_LOCATION (access approximate location only in the foreground)
– ACCESS_FINE_LOCATION (access precise location only in the foreground)
– ACCESS_NETWORK_STATE (view network connections)
– ACCESS_WIFI_STATE (view Wi-Fi connections)
– CAMERA (take pictures and videos)
– FLASHLIGHT
– FOREGROUND_SERVICE (run foreground service)
– FOREGROUND_SERVICE_DATA_SYNC
– GET_ACCOUNTS (find accounts on the device)
– HIDE_OVERLAY_WINDOWS
– INTERNET (have full network access)
– NFC (control Near Field Communication)
– POST_NOTIFICATIONS
– RECEIVE_BOOT_COMPLETED (run at startup)
– RECORD_AUDIO (record audio)
– USE_BIOMETRIC (use biometric hardware)
– USE_FINGERPRINT (use fingerprint hardware)
– VIBRATE (control vibration)
– WAKE_LOCK (prevent phone from sleeping)
– RECEIVE
– BIND_GET_INSTALL_REFERRER_SERVICE
– AD_ID
– DYNAMIC_RECEIVER_NOT_EXPORTED_PERMISSION
It is questionable why an app like Yoti needs access to the Advertising-ID (as we saw this was used by Adjust tracker in the app), precise locations or information about user accounts on the device.
It does not make a privacy-focused impression when permissions like that are claimed, used and – in this case – lead to a non-consensual submission of data to an ad network like Adjust.
As mentioned in the website investigation part of this article, when viewing the privacy notes third party resources are loaded before any user interaction. This is also true for the mobile Android app (very likely also iOS App), because Yoti is using a webview to request and show privacy notes.
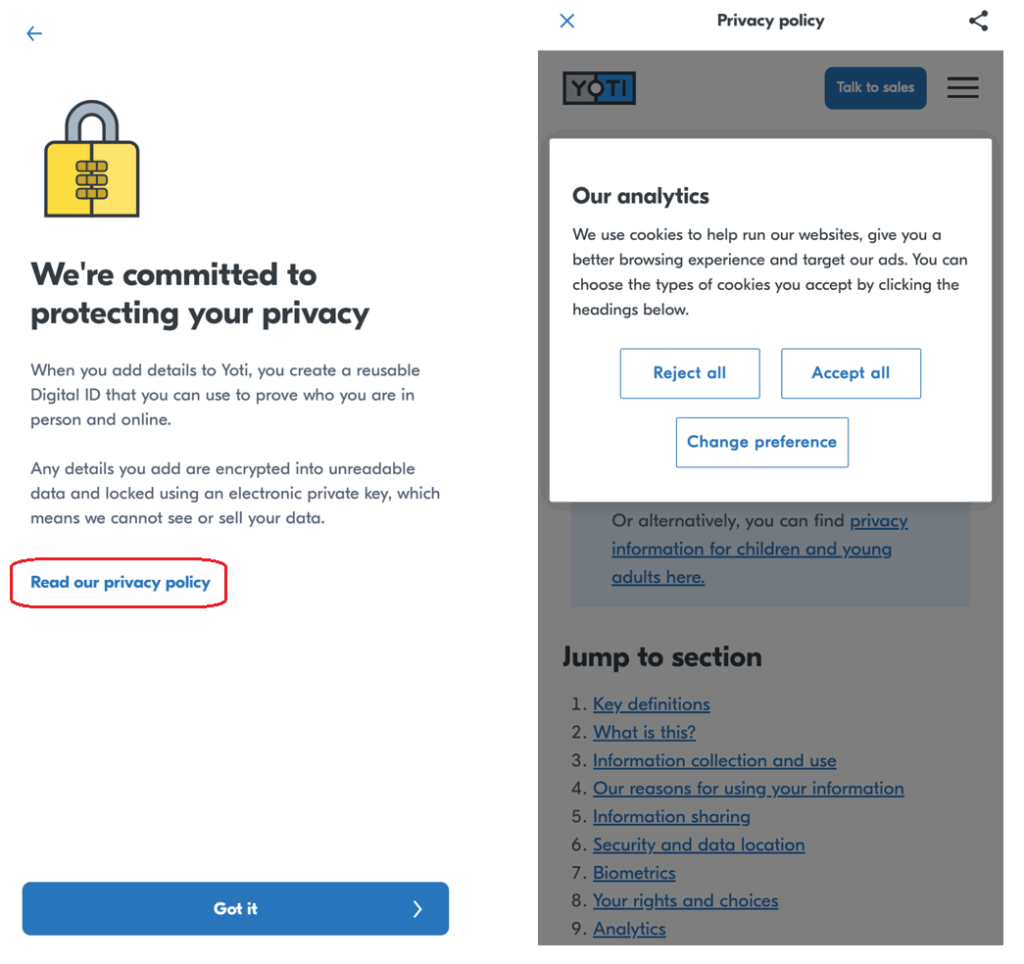
This means that the webpage is loaded and without any explicit user consent a request for third party applications takes place.
Ironically, just before clicking the link to the privacy policy – which lead to a transmission of data – it says “We are committed to protecting your privacy” – the user data (including IP-addresses, which can be considered as personal data under GDPR) is transferred to Google and other third party provider.
When extensively looking into the solution of Yoti and looking for information about the product one can find a reference page from a company in Spain (Málaga) with the name „Algorath“.
Algorath clearly states on their website that they have been contracted by Yoti to develop Yoti’s age verification tool since 2018 and support the training and improvement of the AI models.
Via the certificate transparency log it was possible to track down subdomains from Algorath that were used for purposes connected to Yoti and Yoti’s products.
The endpoints include the following domains:
nuget.yotiai.algorath.com
age.yotiai.algorath.com
sandbox.yotiai.algorath.com
datacollection.yotiai.algorath.com
metadatabe.yotiai.algorath.com
— more —
All domains are hosted in the Google Cloud.
When visiting such a domain a Google login shows up (in most of the cases – in some cases directly tools where accessible). It is possible to authenticate with a normal Google Account.
In some cases, there was no further authorization or protection – which basically means after a login with any Google Account one can make use of potential “internal” tools. In the following case this potentially means that anybody with a Google Account was able to “feed” Yoti’s detection engine with (wrong) data and have an influence on their detection of virtual cameras.
In the screenshot you can see that this is also mentioned as “discrete project” and the warning / note: “If you are going to perform Real data collection and are currently using a virtual camera service, please do not proceed until you disable it.”
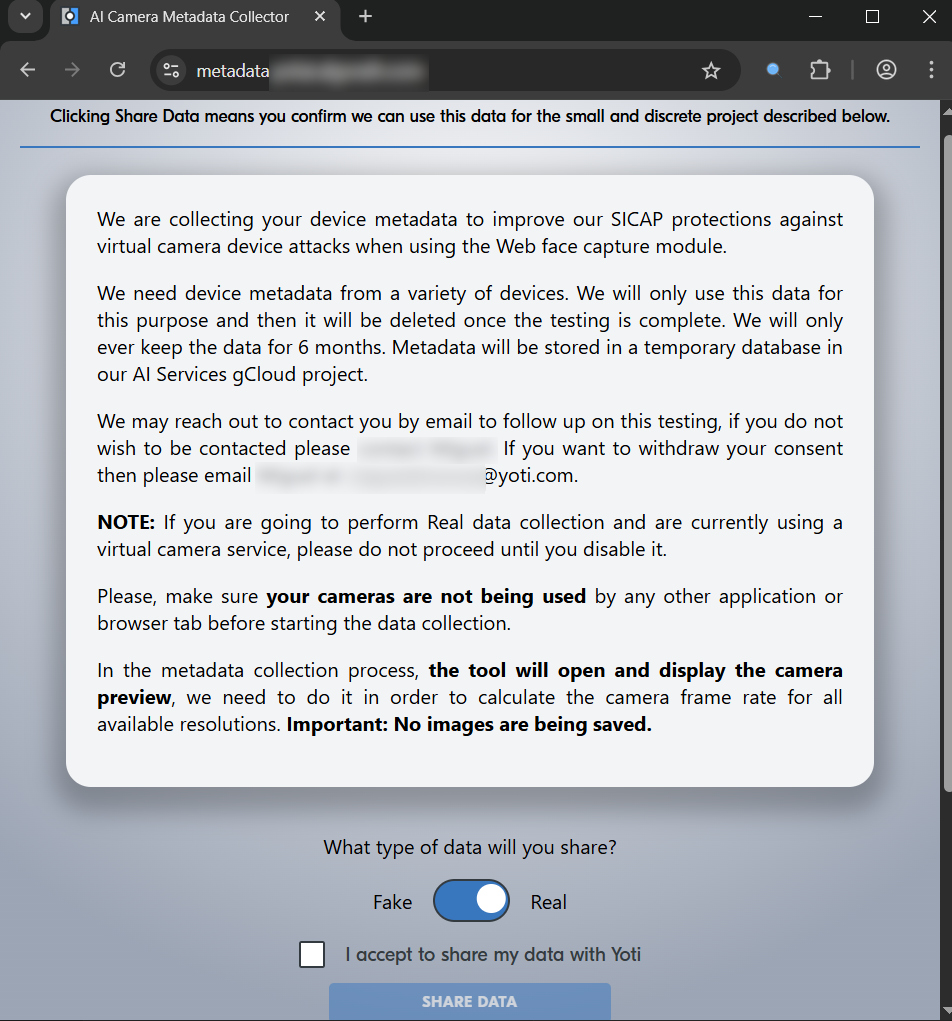
The example shows a web interface from Algorath/Yoti, where a data collection takes place which might later be used to train models to detect virtual cameras. Virtual cameras are a potential way to circumvent age estimation tools like Yoti’s facial scans with deepfakes of a person’s face. Such attacks are often called “digital injection attacks”. In a blog post, Yoti describes its counter measures to defend against such attacks . These measures are described as an additional level of assurance (it seems to be part of the Level 3 “Injection attack detection”), highlighting the importance of fraud detections for Yoti’s business model. The following picture was presented by Yoti end of 2024.
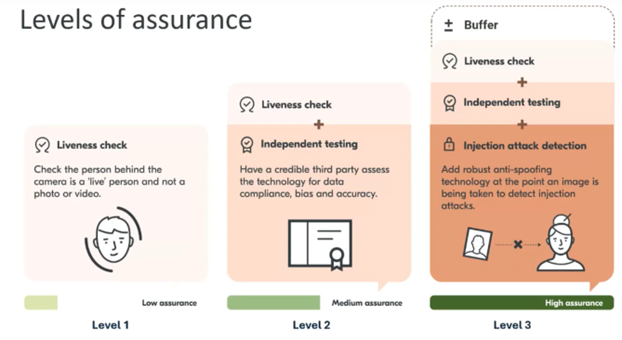
With a lot of training data (for example characteristics and hardware IDs from many cameras) it is easier for Yoti to detect if an end user is not using a physical – but a virtual – camera to circumvent the age verification/estimation system. Via this way Yoti can restrict the access if fraudulent behavior is detected – but there are also enormous risks associated with it.
On the one hand this can lead to so called “false-positives” by mistakenly detecting a physical camera as a virtual one, thereby blocking a user’s legitimate attempt to verify their age. Such false-positives and other technical errors can lead to users losing access to services and content (as some comments from the Google app Rating show):
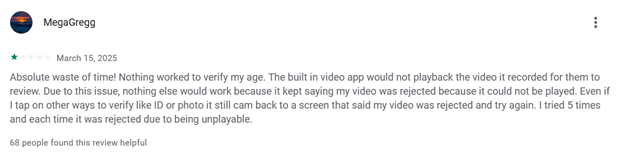
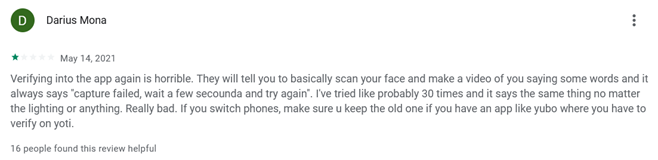
On the other hand, this type of anti-spoofing and fraud detection also is a risk for users’ privacy. To detect illegitimate actions and users a lot of data needs to be processed: Apart from general network information and device information also data from the cameras are used (like framerate or device names and unique identifier).
Via web APIs like “enumeratedevices” Yoti and other age estimation solutions can read out specific devices and their IDs – after users granted permission to the camera (this is generally necessary to use the service). A small proof of concept was implemented and shows that detections or camera fingerprints like that are easily possible.
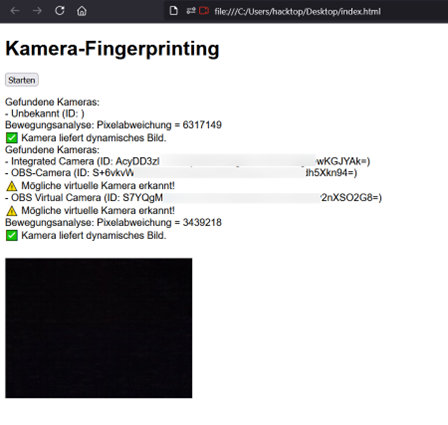
It is likely that due to the improvement of image generators and thus facilitation of creating very good deepfakes, Yoti has decided to follow a two-tired approach to fraud detection by not only focusing on manipulated content, but also on the metadata and devices in use, their behavior and meta data connected with that. In 2022, the Chaos Computer Club has shown that the German “Post-Ident” approach (a identity-verification solution) and other video-based identification mechanisms can easily be tricked.
Other endpoints, with no authorization protection, that could be found via specific subdomains reveal that Yoti has at least 2 AI training models for their age estimation model (March 2023 and August 2024).
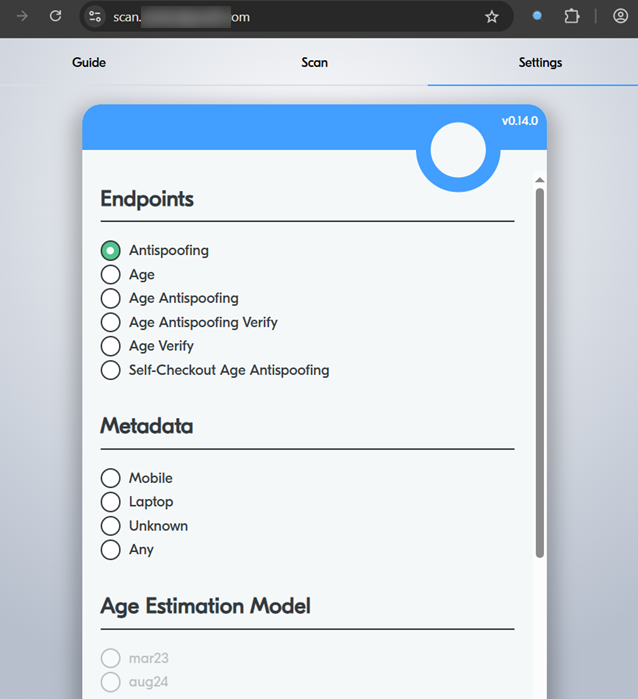
Furthermore, it is possible to select that the transmitted photos can be used for testing – and therefore may have an influence on the AI model of Yoti. This would allow attackers to influence Yoti’s models and would be a so-called AI data poisoning attack. This vulnerability could be abused by attackers to manipulate the output of Yoti’s models, potentially leading to the discrimination of specific groups of users, thereby restricting their legitimate access to content and services.
Another tools (like one for data collection) had slightly better protection:
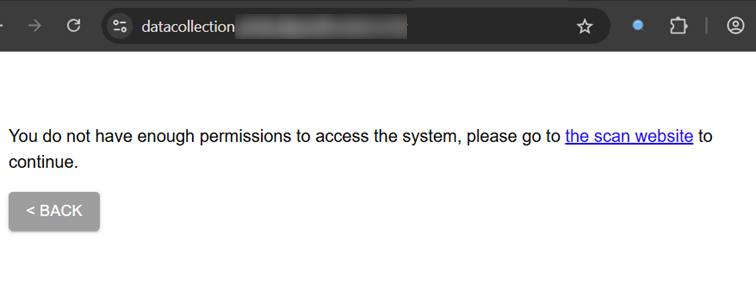
It is plausible that only respective users/roles have access to the system. This is a protection level that should be implemented.
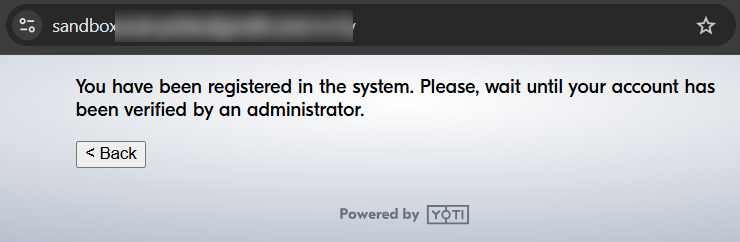
In other cases, it shows that the general user enrollment process was successful, but an administrator must verify the account to grant access (which did not happen).
During this investigation, it was found out that Yoti tracks users extensively and without users’ consent on its website and within its app. Sensible information like the Advertising-ID and other personal-identifiable information are submitted to third parties (like the ad-network Adjust) without consent by default. This behavior is a potential violation of the GDPR which requires clear consent when processing personal-identifiable information and submitting it to third parties.
Additionally, the fraud detection and virtual camera detection of Yoti relies on data that potentially could be manipulated by third parties, which shows how vulnerable an age estimation provider’s supply chain can be. Strong security protections and adequate transparency are necessary measures providers like Yoti should adopt. Also, detection mechanisms like Yoti’s injection attack detection measures highlight the possible adverse effects of fraud detection on users’ privacy. A high detection rate for fraudulent activity will always mean a profound intrusion into users‘ privacy via fingerprinting of metadata and devices.
The general observed behavior conflicts with the company’s mission “to become the world’s most trusted identity platform” – because trust comes from concrete technical implementations, actions and not statements.
We have informed Yoti about our investigation and our observations and will update the blogpost here if we receive any feedback.
Update 1 (04.06.2025, 11:09 Uhr): Yoti has received the submission and will investigate it.
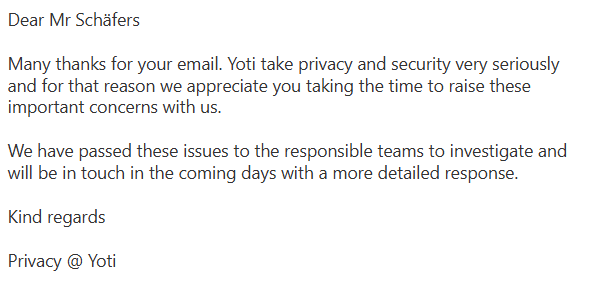
Update 2 (June 12, 2025, 10:06 AM): Upon further inquiry, Yoti stated that they need more time (as different teams are involved).
Update 3 (June 13, 2025, 05:03 AM): Yoti reached out with a full statement. This blogpost now has the concrete subdomains and name of the subcontractor included. Please make sure to read the statement below to get a full picture.


Short summary of the statement (from Yoti):
1.) Yoti states that the named public endpoints pose no threat and were intentionally accessible. Furthermore no data is automatically pulled into Yoti models.
2.) Yoti confirms that the Advertising IDs are used in the Apps, but points out that this processing is at least pseudonymised and refers to legitimate interests of the company to enhance the products.
3.) Yoti confirms that third-party content on the website was inadvertently loaded and that this was a „technical error.“ It also stated that no cookies are set (this was never claimed).
Conclusion
We are happy that Yoti takes our feedback serious and responds quickly to reports like this.
However we do not fully agree with the argumentation from the full statement (especially points 2 and 3). From our point of view and according to GDPR a default processing of the Advertising ID in the Apps is not neccessary/allowed and a clear consent is needed (because it is also forwarded to Adjust).
Furthermore (according to 3) a loading of third party resources on the website still takes place (status: 19.06.2025).
Update 04.08.2025: With the enforcement of the Online Safety Act AVS (as Yoti) were put in place for many websites. There is an ongoing petition in the UK.
Copyright Mint Secure GmbH. All Rights Reserved.